Your OT Systems Are Being Watched — But Not by You.
Every second your industrial control systems are running, silent attackers are looking for their next weakness. What happens when they find it? Production downtime. Compliance penalties. Reputation loss.

Why OT Security is Critical for Your Business
IT (Information Technology) and OT (Operational Technology) serve different purposes—IT secures data, applications, and communication systems, while OT safeguards physical equipment and industrial control systems like PLCs, SCADA, and sensors.
Rising Threats to Industrial Systems
Modern cyberattacks now target industrial systems directly.
- Ransomware can halt factory operations or power distribution.
- Supply chain attacks exploit third-party access to critical infrastructure.
- Legacy vulnerabilities in OT systems—often built without security in mind—remain exposed.
AiCyberWatch: Your OT Security Partner
- Real-time OT threat detection and visibility
- Secure network segmentation and access controls
- 24/7 Managed SOC monitoring for both IT and OT
- Compliance mapping for industrial standards
Your IT network may be strong. But your OT isn’t IT.
Legacy PLCs, SCADA, and ICS weren’t designed to face modern cyberattacks.
Malware doesn’t just steal data — it halts production lines, shuts down plants, and disrupts supply chains.
And when that happens, it’s not just a cyber incident. It’s millions lost in downtime, contracts, and trust.
68% of manufacturing and industrial firms faced at least one OT cyber incident last year.
Common OT Security Risks & How We Mitigate Them
- Legacy Systems Vulnerabilities → Solutions: Patching, segmentation, monitoring.
- Lack of Visibility → Real-time threat detection & asset inventory.
- Convergence of IT & OT → Secure remote access & zero-trust policies.
- Regulatory Compliance (NIST, IEC 62443, NERC CIP) → Compliance-driven security frameworks.

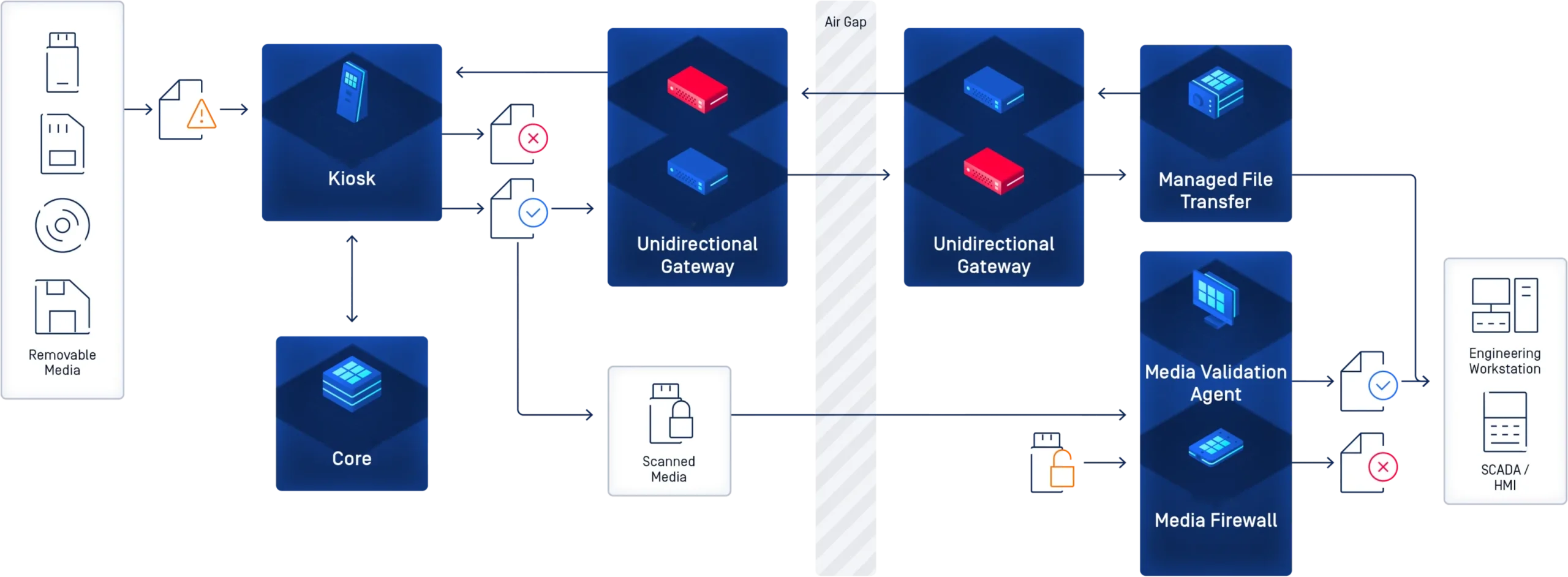
Our OT Security Solutions Include
Comprehensive OT Security Services by AiCyberWatch
OT Risk Assessment &
Penetration Testing
- Identify vulnerabilities in ICS/SCADA systems.
- Simulate attacks to assess security posture.
Network Segmentation &
Micro-Segmentation
- Isolate critical OT assets from IT networks.
- Prevent lateral movement of threats.
Threat Detection &
Response (OT SOC)
- 24/7 monitoring with AI-driven anomaly detection.
- Incident response tailored for industrial environments.
Endpoint Protection for
OT Devices
- Secure PLCs, RTUs, and legacy systems.
- Behavioral analysis to detect malicious activity.
Compliance &
Governance
- Align with IEC 62443, NIST CSF, CISA guidelines.
- Audit-ready documentation & reporting.

Why Choose AiCyberWatch?
Your Trusted Partner in OT Cybersecurity
- Industry Expertise: Specialized in manufacturing, energy, utilities, and critical infrastructure.
- AI-Driven Defense: Leveraging machine learning for proactive threat hunting.
- Customized Solutions: Tailored to your OT environment’s unique needs.
- Proven Track Record: Case studies/testimonials from satisfied clients.
Free OT Security Assessment
Wondering If Your OT Systems Are Secure?
Free gap analysis for the first 10 inquiries.
Ready to Fortify Your OT Infrastructure?
Contact AiCyberWatch today for a consultation.
Phone
FAQs on OT Security
What’s the difference between IT and OT security?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
How often should OT systems be audited?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Can traditional firewalls protect OT networks?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.