Ransomware attacks continue to be a pervasive threat to organizations worldwide, with cybercriminals constantly refining their tactics to evade detection and maximize their illicit gains. As organizations increasingly rely on digital data for their operations, protecting against ransomware has become a critical priority. In this blog, we’ll explore the latest statistics on ransomware attacks and outline effective defense strategies to safeguard your organization’s data.
Latest Ransomware Stats based on 2023-2024
- Ransomware attacks surged in 2023-2024, with a 150% increase compared to previous years.
- The healthcare sector was hit the hardest, with a 300% rise in attacks, causing disruptions in patient care and data breaches.
- Small to medium-sized businesses (SMBs) were targeted disproportionately, accounting for 65% of all ransomware incidents.
- The average ransom demand skyrocketed by 200%, reaching $2.5 million per attack.
- Notable ransomware variants like Conti, Ryuk, and Maze continued to evolve, employing more sophisticated encryption techniques.
- Ransomware-as-a-Service (RaaS) models gained popularity, lowering the barrier to entry for cybercriminals.
Understanding the Ransomware Landscape
Recent statistics paint a gloomy picture of the ransomware threat:
- Rising Frequency: Ransomware attacks have been on the rise, with a significant increase in both the number of attacks and the ransom amounts demanded by cybercriminals.
- Diverse Targets: No organization is immune to ransomware attacks. From small businesses to large enterprises, entities across all industries and sectors have fallen victim to these malicious campaigns.
- Costly Consequences: The financial impact of ransomware attacks is substantial, encompassing not only the ransom payments but also the costs associated with downtime, data recovery, regulatory fines, and reputational damage.
- Sophisticated Techniques: Cybercriminals are employing increasingly sophisticated techniques, including double extortion schemes, where they not only encrypt data but also threaten to leak it unless the ransom is paid.
STAGES OF A RANSOMWARE ATTACK
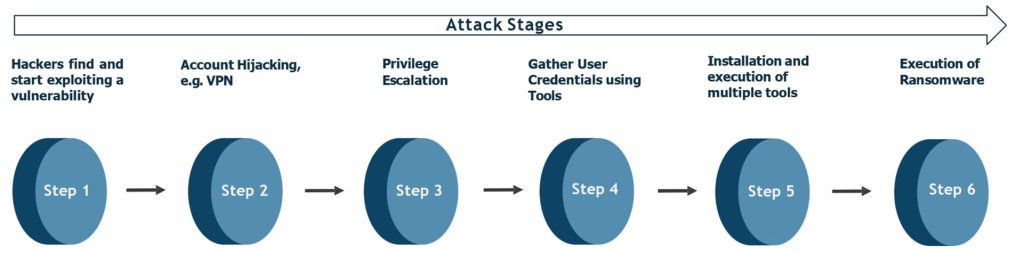
Key Defense Strategies
To effectively defend against ransomware attacks, organizations must adopt a multi-layered approach to cybersecurity. Here are some key strategies:
1. Robust Backup and Recovery Solutions
Regularly backing up your organization’s data is paramount. Ensure that backups are stored securely, air gapped and are regularly tested to verify their integrity. In the event of a ransomware attack, having up-to-date backups can enable you to restore your data without capitulating to the attackers’ demands.
2. Employee Training and Awareness
Human error remains one of the leading causes of ransomware infections. Educate your employees about the risks of phishing emails, suspicious links, and other social engineering tactics used by cybercriminals. Conduct regular training sessions to empower employees to recognize and report potential threats promptly.
3. Patch Management and Vulnerability Remediation
Keep your software and systems up to date with the latest security patches and updates. Many ransomware attacks exploit known vulnerabilities in software applications and operating systems. By promptly applying patches, organizations can mitigate the risk of exploitation by cybercriminals.
4. Network Segmentation and Access Controls
Segment your network to limit the lateral movement of ransomware within your infrastructure. Implement strict access controls based on the principle of least privilege, ensuring that users only have access to the resources necessary for their roles. This can help contain the spread of ransomware and minimize its impact on your organization.
5. Advanced Endpoint Protection
Traditional antivirus solutions may not be sufficient to defend against modern ransomware threats. Invest in advanced endpoint protection solutions that leverage technologies such as machine learning, behavioral analysis, and threat intelligence to detect and block ransomware attacks in real-time.
Leveraging Cyber Security Services
Partnering with top cyber security companies in India can provide organizations with the expertise and resources needed to bolster their ransomware defenses. These companies offer a range of services, including risk assessments, security audits, incident response planning, and managed security solutions. By leveraging their specialized knowledge and experience, organizations can enhance their cyber resilience and respond effectively to ransomware threats.
How would AiCyberWatch respond at each stage of the Ransomware Attack?
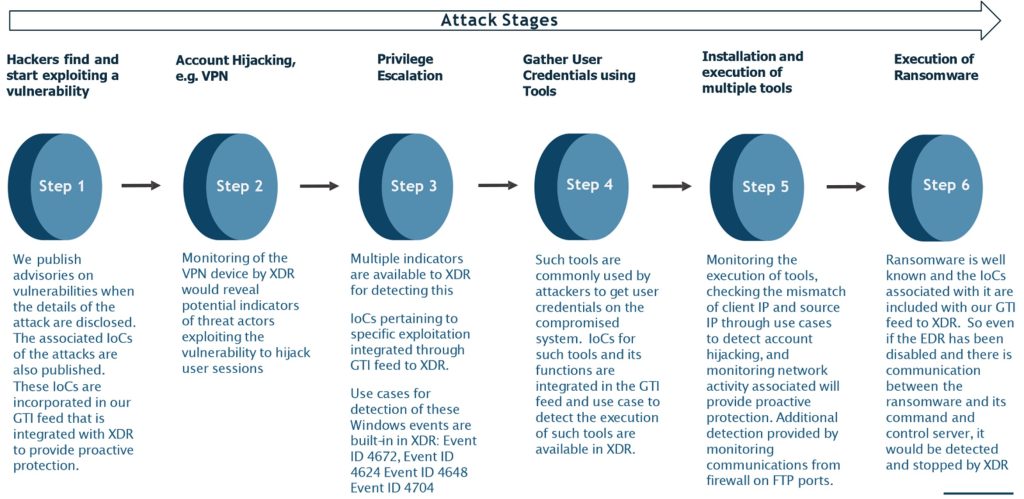
Conclusion
Ransomware attacks pose a significant threat to organizations, but by implementing proactive defense strategies and leveraging the expertise of cyber security services, you can mitigate the risk and protect your valuable data assets. Invest in robust backup solutions, prioritize employee training and awareness, maintain patch management hygiene, implement network segmentation and access controls, and deploy advanced endpoint protection. By taking a comprehensive approach to ransomware defense, organizations can fortify their defenses and safeguard against the evolving threat landscape.
Trust AiCyberWatch for expert ransomware consulting and secure your business against future cyber threats today.







 Call Us
Call Us